The trader took advantage of the fact that there wasn’t enough money in the market by changing the price of MNGO on the decentralized exchange Mango.

A bad crypto trader used millions of dollars to rig the prices of Mango’s MNGO tokens on its own decentralized exchange (DEX) to drain over $116 million from the platform.
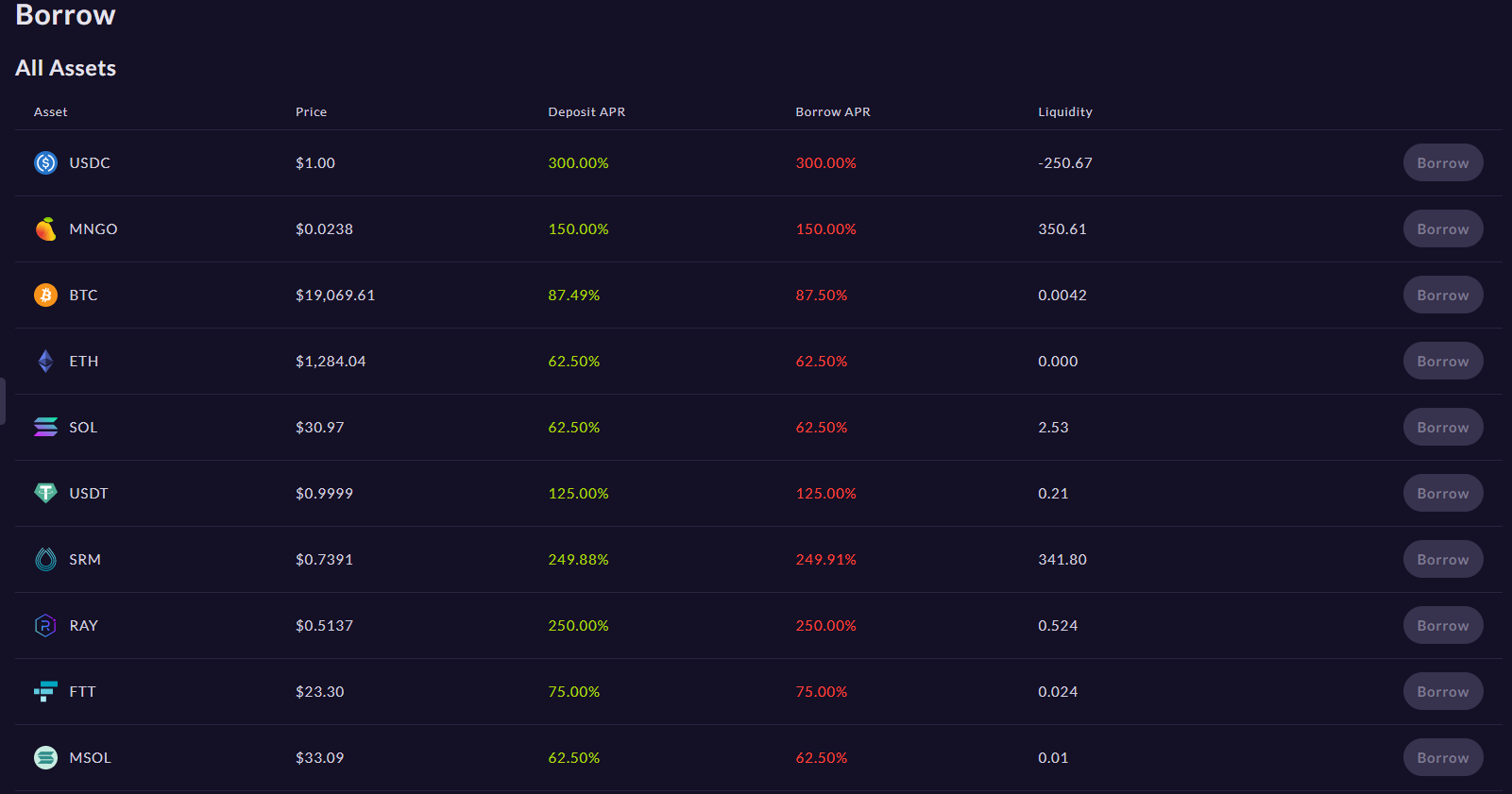
The exchange has a low-cost on-chain trading interface that lets people trade spot and perpetual futures. According to data from CoinGecko, about $30 million worth of cryptocurrency was traded on the exchange in the last 24 hours.
The decision was made because of the ongoing drama over bad debt in the Solana DeFi ecosystem, which involved Solend and Mango lending apps.
As was reported this morning, Mango and Solend worked together earlier this year to raise money to save a large Solana whale with $207 million in debt spread across multiple lending platforms. This move was meant to protect the Solana ecosystem from losses if the whale’s position were to be liquidated.
How the event went down
Solana-based Like other DEXs, Mango matches trades between users of decentralized finance (DeFi) by using smart contracts.
This is very important to understand how the heist happened: Smart contracts are completely decentralized and are not overseen by a central party. This means that a bad trader can use enough money to take advantage of flaws in any protocol without anyone being able to stop the attack before it happens.
The attack was done with the help of two accounts. On account “A,” the trader used 5 million USD Coin (USDC) to buy 483 million MNGO and “short” the asset, which means to bet against it.
Then, on account “B,” the trader used another 5 million USDC to buy the same amount of MNGO. In total, he used 10 million USDC to effectively hedge his position, as shown by data on Mango from Joshua Lim, head of derivatives at Genesis.
The trader then used more money to buy more spot MNGO tokens. In just ten minutes, the price went from 2 cents to as high as 91 cents. This was possible because spot MNGO was a token that wasn’t traded much and had low liquidity. This made it easy for the bad trader to change prices quickly.
As the spot price of MNGO went up, the trader’s account “B” quickly racked up $420 million in profits that he or she never got to keep. The attacker then sold more than $116 million worth of all the tokens on Mango, which wiped out the protocol in a sense.
Spot MNGO prices soon went back to 2 cents, which was less than what the trader initially paid for MNGO futures on account “A.” At the time this was written, that trader’s account had more than $6 million in profits, but there wasn’t enough cash on the platform to pay him out.
Overall, the bad trader used more than 10 million USDC to take out more than $116 million from Mango. He or she did this while paying very little in fees and staying within the rules of the platform. Mango wasn’t hacked, it worked exactly as it was supposed to, and a smart trader with bad intentions was able to get token liquidity out of the system.
It’s important to note that the above manipulative strategy won’t work on two centralized exchanges. If a trader placed high bids on one venue, prices would automatically go up on that exchange, and other exchanges would immediately raise the prices of assets on their own systems. This means that the strategy is unlikely to make any money.
The developers of Mango said early Wednesday that they had looked into the exploit and that broken oracles were to blame. Oracles are outside tools that bring information from outside a blockchain into it.
Some people thought that data provider Pyth was the oracle, which a key Pyth backer backed up. “The attacker bought and sold the thinly traded mango token,” Kanav Kariya, president of Jump Crypto, a crypto fund that has put a lot of money into Pyth, said in a tweet.
“Oracles only say the price. “Pyth/Switchboard reported the prices on exchanges correctly,” Kariya said. In the last 24 hours, MNGO has dropped by 40%.
