Google Cloud’s threat intelligence reveals North Korean-backed cyber attackers targeting Brazil’s cryptocurrency exchanges and fintech firms for hijacking, extortion, and fraud.
The threat intelligence department of Google Cloud has identified that cyber assailants affiliated with the North Korean government are currently conducting an active campaign against Brazil’s fintech companies and cryptocurrency exchanges.
The coordinated endeavors to commandeer, extort, and defraud Brazilian individuals and organizations were emphasized in the June 13 Google threat intelligence report.
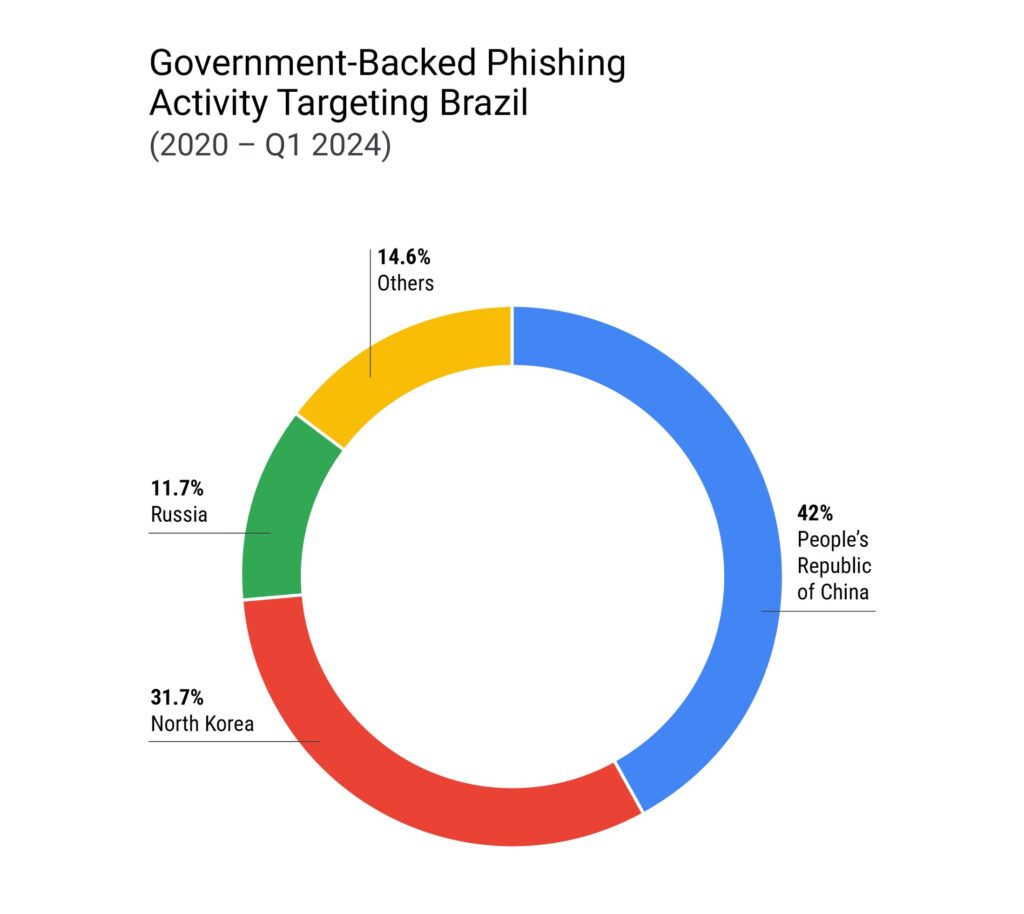
Although North Korean groups concentrate on cryptocurrency firms, aerospace and defense, and government entities, cyber criminals who are supported by the Chinese government prefer to target only the energy sector and government organizations in Brazil.
The employment market has been the target of the notorious North Korean cybercriminal group, Pukchong (also known as UNC4899), which has targeted Brazilian citizens and organizations. They deceived job seekers into downloading malware onto their devices. In accordance with the report:
“The project was a trojanized Python app for retrieving cryptocurrency prices that was modified to reach out to an attacker-controlled domain to retrieve a second stage payload if specific conditions were met.”
Similarly, GoPix and URSA were observed to be actively targeting Brazilian crypto firms in malware attacks.
Trust Wallet, a crypto wallet provider, recently requested that Apple users disable iMessage. The company cited “credible intel” of a zero-day exploit that could enable hackers to take control of users’ phones.
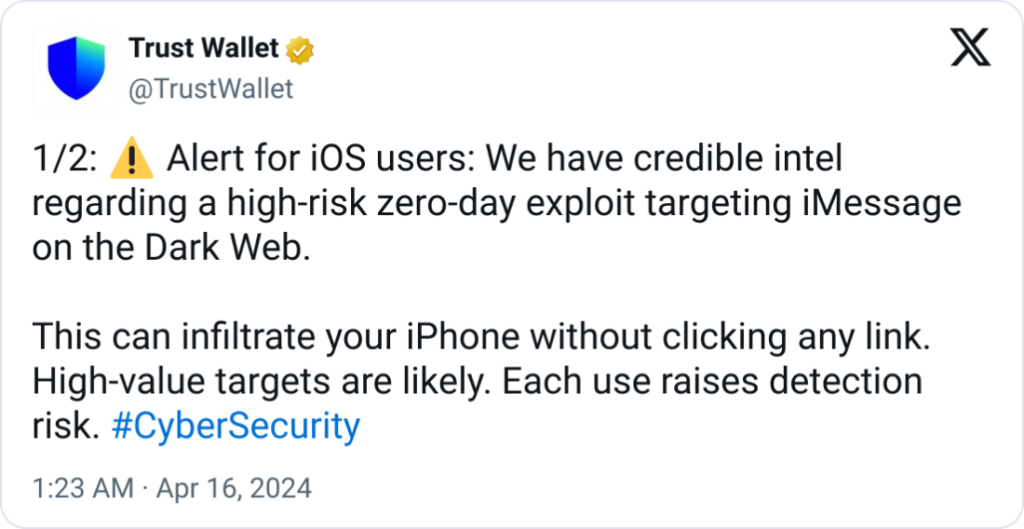
A zero-day exploit is a type of cyberattack that exploits an unidentified or unaddressed security vulnerability in computer software, hardware, or firmware.
Kaspersky, a cybersecurity firm, recently discovered that Kimsuky, a North Korean hacking group, employed a “striking” new malware variant known as “Durian” to initiate attacks on South Korean crypto firms.
Kaspersky stated that Durian has a comprehensive backdoor functionality that allows for the implementation of commands, the downloading of additional files, and the exfiltration of files.
Furthermore, Kaspersky observed that LazyLoad was also employed by Andariel, a sub-group within the Lazarus Group, a North Korean hacking consortium, which implies a “tenuous” connection between Kimsuky and the more notorious hacking group.
