Euler Finance, a cryptocurrency lending platform, has disclosed the findings of 29 audit reports from 12 distinct cybersecurity firms in connection with its “v2” relaunch. AC

The reports indicate that all security concerns have been satisfactorily resolved, as indicated by the announcement. The protocol also had a public $1.2 million post-audit bug bounty, which yielded no medium or higher severity issues.
The announcement announced that Euler’s security was fortified before its relaunch, with a total expenditure exceeding $4 million.
A flash loan attack on March 13, 2023, resulted in exploiting the previous iteration of Euler for $195 million. Subsequently, the assailant reimbursed the entire sum.
The new version of Euler has undergone “one of the most expensive and comprehensive security processes for any DeFi protocol to date,” according to the announcement.
To develop v2, EulerDAO, Euler’s decentralized autonomous organization, allocated over $11 million to the development team. Of this amount, over $4 million was allocated to security. Using these security funds, the team recruited additional personnel to ensure that the protocol complies with the ISO27001 standards utilized by banks and defense companies.
Various external specialists were engaged to develop attack vectors and challenge the security of Euler v2. These specialists comprised two security engineers from Web3 security firm Certora, Yield protocol co-founder Alberto Cuesta Cañada, and Spearbit security researchers Cmichel and StErMi, among others.
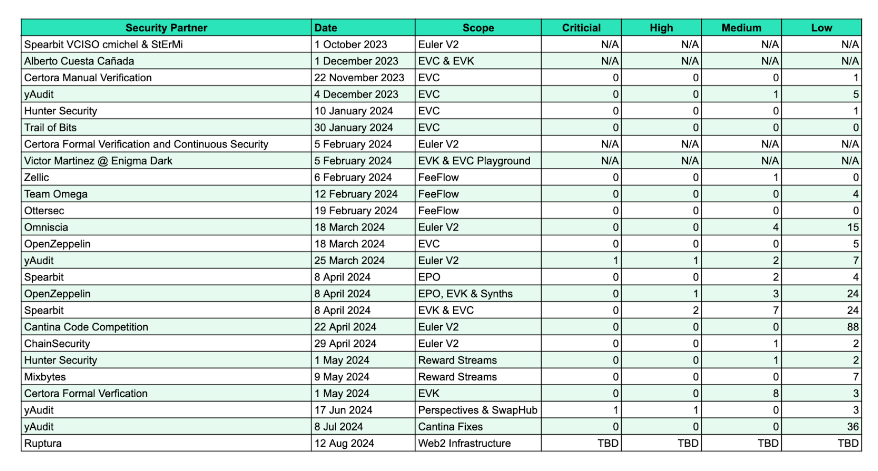
After completing the code, the team engaged 12 cybersecurity firms to audit each Euler module. A total of 29 audits have been completed thus far.
Spearbit, Certora, Hunter Security, Trail of Bits, Zellic, OpenZeppelin, Chain Security, Hunter Security, Omniscia, yAudit, Ruptura, and other auditors were among the participants. The auditors identified five high-severity vulnerabilities and two critical-severity vulnerabilities, which were subsequently resolved.
Upon concluding the third-party audits, the team initiated a $1.25 million bug bounty contest to ascertain whether the auditors had overlooked any vulnerabilities. The bug bounty participants were unsuccessful in identifying any defects of critical, high, or medium severity. The team distributed $200,000 to participants who identified low-severity vulnerabilities.
The team’s blog post on February 22 indicated that v2 will offer new features, including synthetic assets, customizable vaults, and a fee auction mechanism, in addition to these security enhancements.
March 2023 saw the exploitation of the original version of Euler through a flash loan attack. The perpetrator employed two distinct accounts. First, the account borrowed from the protocol and utilized a “donate” function to force itself into default.
The attacker’s second account liquidated the first account once it defaulted. In the second account, the perpetrator acquired more assets than they lost in the first, resulting in a profit of over $195 million due to the generous discounts granted to liquidators in Euler v1.
The exploiter returned the plundered funds just 23 days after the attack. The Euler assault was the most significant decentralized finance exploit of 2023.
