A newly detected malware on Apple’s macOS associated with the North Korean hacking group Lazarus reportedly targets blockchain engineers of cryptocurrency exchange platforms.

Analysis by Elastic Security Labs reveals that the covert backdoor of the malicious software “KandyKorn” for macOS can perform the following operations: data retrieval, directory listing, file upload/download, secure deletion, process termination, and command execution.
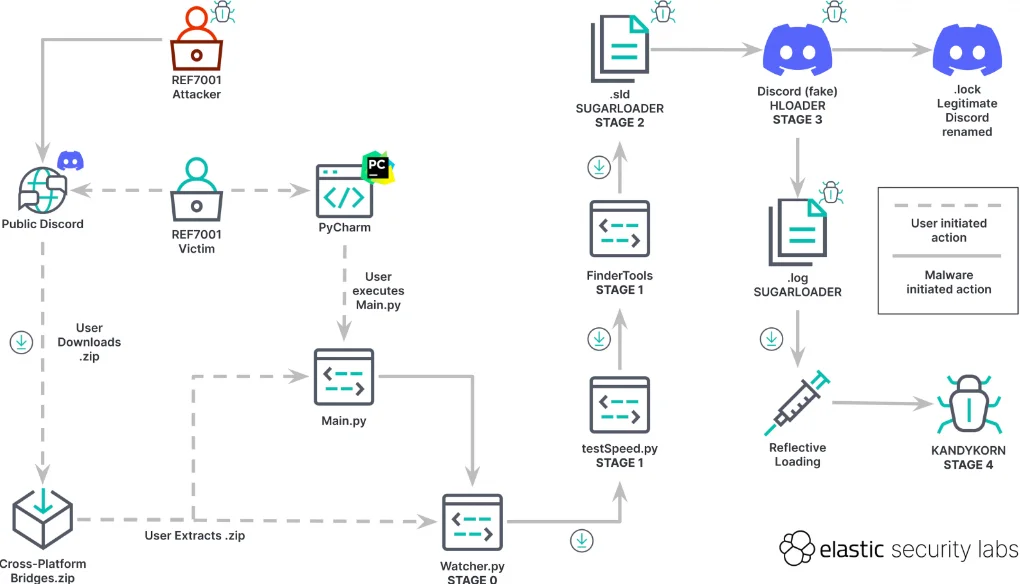
The preceding flowchart delineates the sequential actions executed by the malware to compromise and seize control of users’ computers. The perpetrators initially disseminated Python-based modules through Discord channels by assuming the identities of community members.
Succumbing to an arbitrage algorithm that is specifically engineered to generate profits automatically, the social engineering assaults deceive members of the community into downloading a hazardous ZIP archive bearing the name ‘Cross-platform Bridges.zip.’
Nevertheless, thirteen malicious modules are imported into the file and collaborate to take and manipulate data. The report was as follows:
“We observed the threat actor adopting a technique we have not previously seen them use to achieve persistence on macOS, known as execution flow hijacking.”
Motivated primarily by financial gain and not espionage, their other principal operational focus, Lazarus, continues to target the cryptocurrency industry.
The presence of KandyKorn emphasizes that Lazarus has a clear intention of targeting macOS, demonstrating the threat organization’s exceptional capability to develop subtle yet sophisticated malware specifically designed for Apple computers.
A popular Telegram bot known as Unibot, which was recently exploited to snipe transactions on the decentralized exchange Uniswap, caused the token’s price to plummet by 40% in a single hour.
Consequent to the notification of Unibot users by the blockchain analytics firm Scopescan regarding an ongoing intrusion, an official source subsequently corroborated the situation:
“We experienced a token approval exploit from our new router and have paused our router to contain the issue.”
Unibot has pledged to provide compensation to all users who incurred financial losses as a result of the contract exploit.
