In fresh research, the blockchain security company CertiK claims that Telegram Messenger users are vulnerable to malicious attacks due to a significant vulnerability.

On April 9, CertiK Alert used the social media platform X to alert users to a “high-risk vulnerability in the wild” that might enable hackers to use Telegram’s media processing to launch a remote code execution (RCE) attack.
The post claims that a “possible RCE” exploit in Telegram’s media processing in the Telegram Desktop application has been found by CertiK’s team.
“This vulnerability puts users at risk of malicious attacks via carefully crafted media files, like pictures or videos,” stated CertiK.
Users should verify their Telegram Desktop configuration and turn off the auto-download option to prevent the vulnerability. You can turn off the feature by selecting “Advanced” from the “Settings” menu.
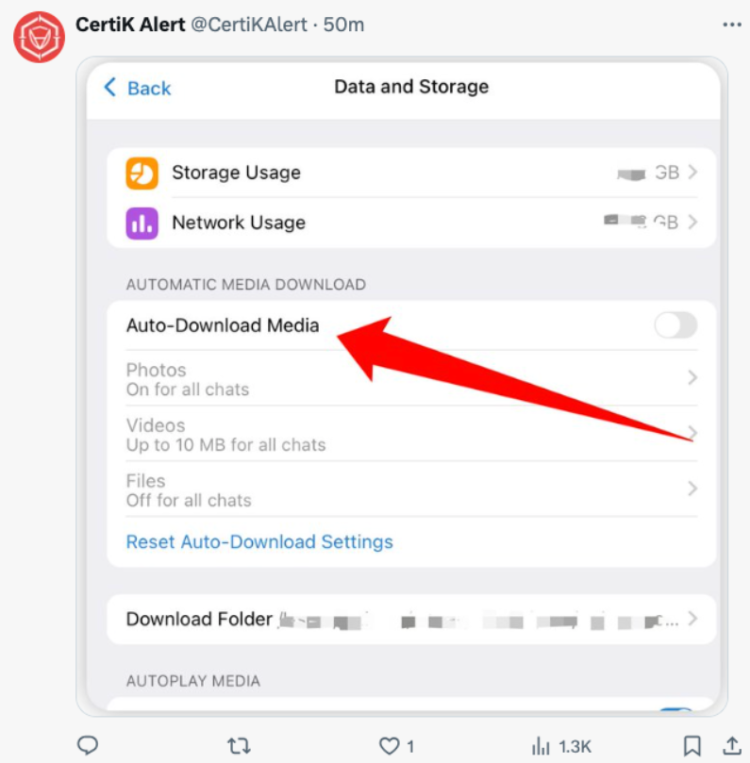
“Disable auto-download for photos, videos, and files across all chat types (private chats, groups, and channels) under the ‘Automatic Media Download’ section,” said CertiK.
At the time of publication, Cointelegraph had not heard back from CertiK or Telegram regarding the new vulnerability in Telegram.
With its custodial wallet solution, Wallet, users may transact cryptocurrencies like Bitcoin and Toncoin (TON) and communicate with each other using Telegram, a popular chat that supports cryptocurrencies.
“Custodial” refers to Wallet placing the assets in its own custody rather than providing users with the private key by default to shield novices in the market from assuming self-custody obligations.
Telegram has had vulnerabilities before, this being only the most recent one. A Google engineer, Dan Reva discovered a severe flaw in 2023 that would let intruders turn on the microphone and camera on macOS laptops.
A security researcher from Shielder found a similar media-related problem on Telegram in 2021. This bug allowed attackers to send animated stickers that were altered, potentially exposing the victims’ data.
However, Telegram has been aggressively patching any holes in its program. Since its launch in 2014, Telegram’s bug bounty program has allowed developers and security researchers to submit reports and potentially earn prizes of up to $100,000, depending on the severity of the issue.
