This cunning malware, which masquerades as legal desktop software, has infected thousands of computers across 11 countries, forcing people to unintentionally mine Monero (XMR).
According to a recent study, crypto mining malware has been covertly infecting millions of machines worldwide since 2019 by disguising itself as trusted applications like Google Translate.
The virus has been evading detection for years, according to a paper released on August 29 by Check Point Research (CPR), a research group for the American-Israeli cybersecurity business Check Point Software Technologies.
In part because of its cunning architecture, which postpones the crypto mining virus installation for weeks after the first program download.
The malware application infects PCs using fake desktop versions of well-known programs like YouTube Music, Google Translate, and Microsoft Translate. It is linked to a Turkish-speaking software developer that advertises “free and secure software.”
A covert Monero (XMR) crypto mining business is set up after a virus installation procedure is progressively initiated via a scheduled task mechanism over the course of many days.
The cybersecurity company said that the “Nitrokod” crypto miner, which has its headquarters in Turkey, had infected computers in 11 different nations.
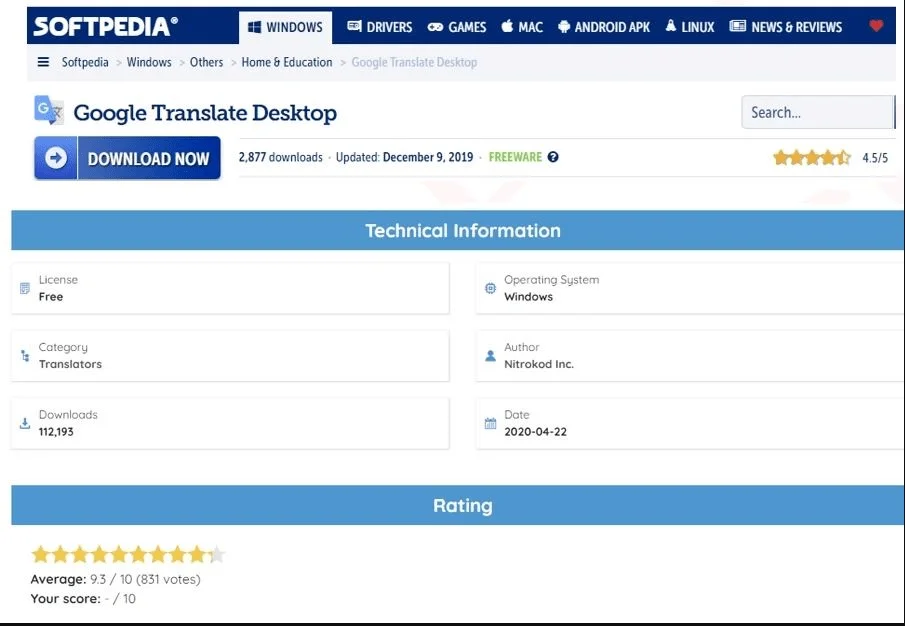
For CPR, counterfeit versions were offered on well-known software distribution websites like Softpedia and Uptodown under the publication name “Nitrokod INC.”
Even though Google doesn’t have an official desktop version of that software, the phony desktop version of Google Translate on Softpedia had almost a thousand ratings and an average star rating of 9.3 out of 10. Some of the apps had been downloaded hundreds of thousands of times.
Check Point Software Technologies claims that a crucial element of the fraud is providing a desktop version of the programs.
Since most Nitrokod apps don’t have desktop versions, people who believe they’ve uncovered a program that’s not accessible elsewhere may be drawn to the fake software.
The malware-filled fakes may also be found “by a simple online search,” claims Maya Horowitz, VP of Research at Check Point Software.
“What’s most interesting to me is the fact that the malicious software is so popular, yet went under the radar for so long.”
The Google Translate Desktop ripoff from Nitrokod is still one of the top search results as of this writing.
Malware Design helps avoid detection
Because the phony applications may imitate the same features that the real apps provide, it might be difficult to identify the virus even after the user opens the bogus program.
Using a Chromium-based framework, the majority of the hacker’s applications are quickly generated from the official websites, enabling them to distribute usable apps laced with malware without having to create them from scratch.
Israel, Germany, the United Kingdom, America, Sri Lanka, Cyprus, Australia, Greece, Turkey, Mongolia, and Poland are just a few of the countries that have had over 100,000 victims of the virus so far.
Horowitz claims a few simple security practices may help lower the danger of being duped by this virus and others like it.
“Beware of lookalike domains, spelling errors in websites, and unfamiliar email senders. Only download software only from authorised, known publishers or vendors and ensure your endpoint security is up to date and provides comprehensive protection.”
