Following the Ether exploit on Munchables, the developer hacker, who stole $62.8 million worth of Ether , has decided to return the funds without demanding a ransom after eight hours.

At approximately 9:30 pm UTC on March 26, Munchables, an Ethereum-based nonfungible token (NFT) game, disclosed a breach that compromised the GameFi application, resulting in more than 17,400 ETH loss.
Munchables and blockchain investigators, including ZachXBT and PeckShield, initiated the monitoring of the whereabouts of the stolen funds to apprehend them.
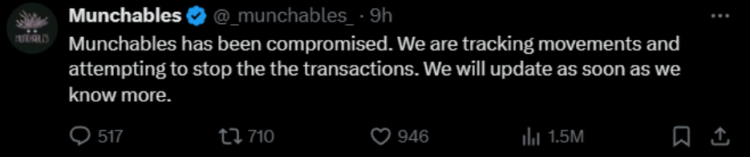
According to ZachXBT, the exploit originated from the Munchables team’s employment of a North Korean developer with the alias “Werewolves0943.”
Munchables identified the intruder as one of its developers at 4:40 am UTC on March 27. Following an hour of negotiations, the erstwhile developer consented to the return of the compromised funds. As stated in a formal statement by Munchables:
“The Munchables developer has shared all private keys involved to assist in recovering the user funds. Specifically, the key which holds $62,535,441.24 USD, the key which holds 73 WETH, and the owner key which contains the rest of the funds.”
Under the alias Pacman, the Ethereum layer-2 blockchain Blast developer thanked ZachXBT for his assistance and declared that “the former Munchables developer ultimately decided to return all funds without demanding a ransom.”
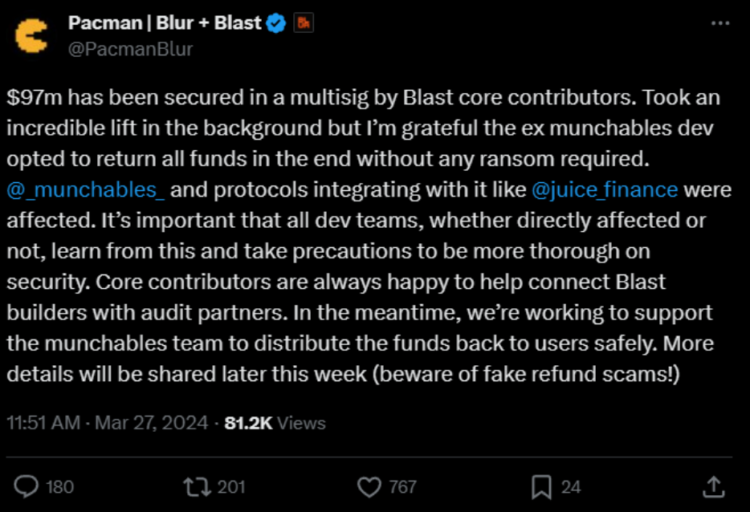
Being a member of the Munchables team, Pacman will assist in redistributing the unlawfully acquired funds, given that Munchables was constructed atop the Blast blockchain.
Victims of the breach are advised to ensure they only follow communications from reputable sources in the interim to prevent falling victim to refund schemes.
Four days before the exploit, an individual breached four distinct decentralized finance (DeFi) aggregator ParaSwap addresses and seized approximately $24,000. After recovering the funds, the protocol initiated the process of refunding users.
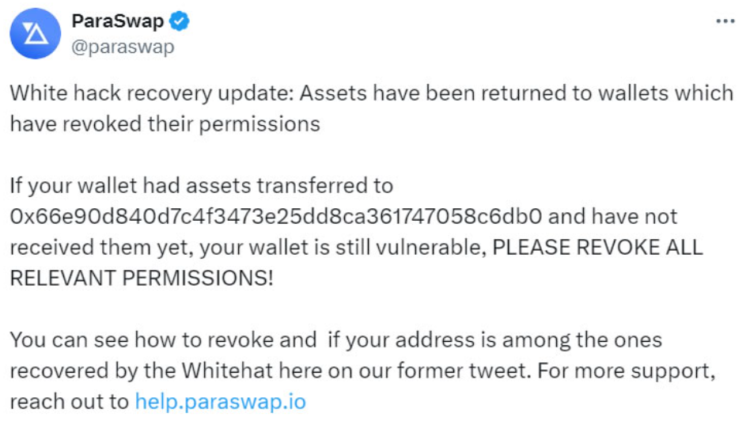
White hat hackers assisted ParaSwap in resolving the issue and revoking authorizations for the susceptible AugustusV6 smart contract.
The vulnerability impacted 386 addresses in total, according to ParaSwap. As of March 25, 213 addresses still need to revoke allowances for the defective contract.
