In recent years, the North Korean government (DPRK) has allegedly used numerous hacking groups, most notably the Lazarus Group, to seal crypto.

Hackers linked to the North Korean government have reportedly broadened their social engineering schemes to steal cryptocurrencies by infiltrating “hundreds” of multinational IT companies.
North Korean Hacking Groups Identified
At the Cyberwarcon cybersecurity conference, researchers highlighted two North Korean hacker groups, “Sapphire Sleet” and “Ruby Sleet,” according to a report by TechCrunch.
Sapphire Sleet targeted individuals through fraudulent job schemes, pretending to be legitimate recruiters.
They lured victims into interviews and then infected their computers with malware disguised as PDF files or malicious links during the recruitment process.
Ruby Sleet focused on infiltrating aerospace and defense contractors in the United States, the United Kingdom, and South Korea to steal military secrets.
The report also revealed that North Korean IT workers used AI-generated fake identities, social media profiles, and voice-altering technologies to infiltrate companies and execute recruitment scams.
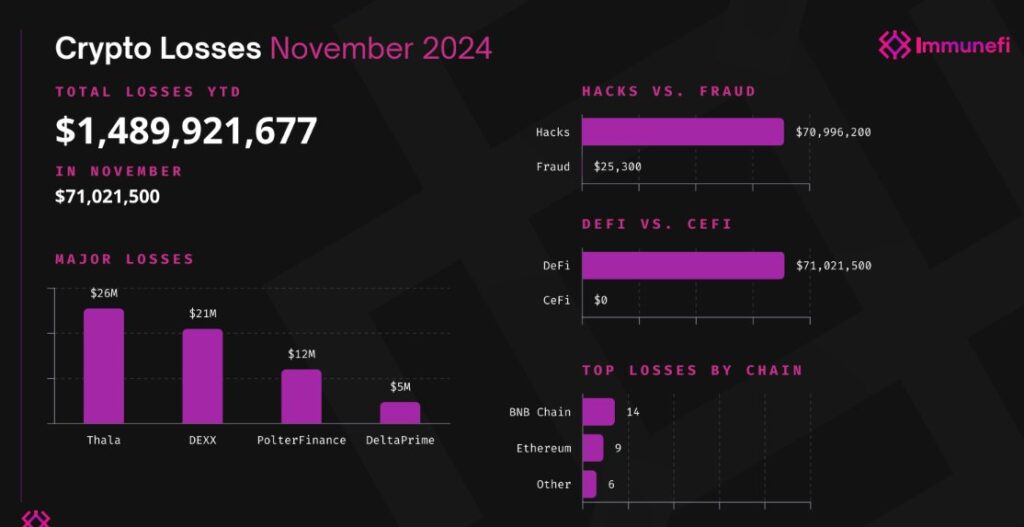
Cryptocurrency Industry in the Crosshairs
Long before the Cyberwarcon findings, North Korean hackers had been targeting cryptocurrency firms with similar tactics.
In August, blockchain investigator ZachXBT identified 21 developers, allegedly North Korean, working on various crypto projects using fabricated identities.
In September, the FBI warned that North Korean hackers were targeting crypto companies and decentralized finance (DeFi) projects.
These attacks involved malware disguised as job offers, which stole users’ private keys when downloaded or accessed through malicious links.
In October, concerns arose within the Cosmos ecosystem over its Liquid Staking Module, reportedly developed by North Korean hackers.
Jacob Gadikian, a Cosmos ecosystem developer, remarked, “The people who built the LSM are the world’s most skilled and prolific crypto thieves.” These fears prompted multiple security audits of the Liquid Staking Module to detect potential backdoors or harmful code.
