Last year, the Russian hacker group Darkside compromised the computer systems of Colonial Pipeline by using a single stolen password.

According to a new analysis released on Monday by blockchain analytics firm Chainalysis, over 74% of ransomware money was channelled through high-risk wallet addresses likely headquartered in Russia last year, totalling over $400 million USD. The analysis looked at ransomware intrusions in 2021 and concluded if they were linked to Russia based on three crucial characteristics.
Evil Corp, a Russian cybercriminal gang with purported links to the Russian government, was suspected of being behind a particular intrusion.
Only non-former-Soviet country victims are targeted by ransomware.
Ransomware variants that distribute Russian-language papers and announcements
In addition to the selection criteria, online traffic data appears to suggest that Russia is where the great bulk of extorted monies are laundered. Another 13% of cash received from ransomware addresses to services went to users in Russia, which is more than any other country.
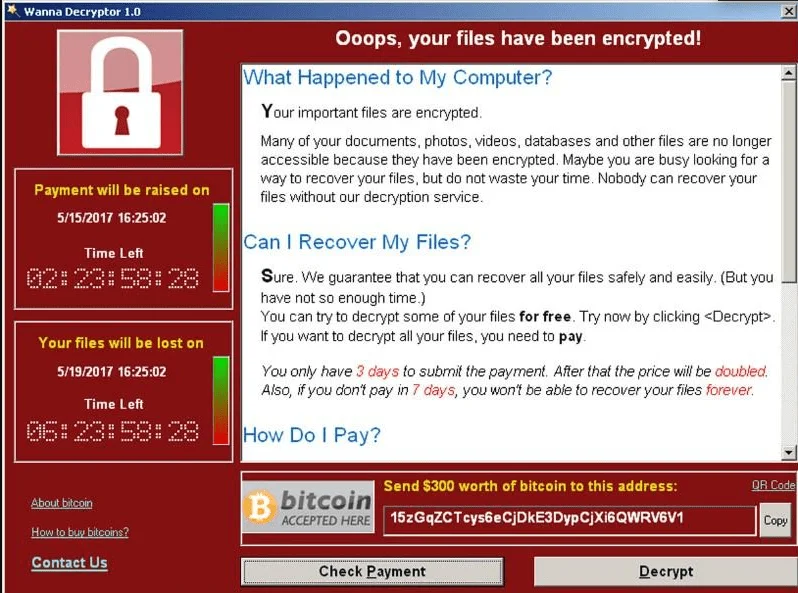
Typically, ransomware infects a user’s computer through a program vulnerability, or by downloading unknown files, etc. They then encrypt the victim’s files and demand payment in Bitcoin (BTC) or Monero (XMR) to a wallet address in order to get access to the data.
Last year, the Russian hacker group Darkside compromised the computer systems of Colonial Pipeline by using a single stolen password. As a result, the pipeline’s operators were compelled to pay a crypto ransom of more than $4 million (of which $2.3 million was recovered) in order to regain access to their encrypted files, but not before triggering a momentary gasoline shortage.