With the widespread acceptance of cryptocurrencies in recent years, the need for secure cryptocurrency wallets has grown significantly. But with so many types of crypto wallets available, it would take time to identify a safe and functional wallet.

Wallets are essential for safeguarding your investments but picking the best one can be challenging. Your cryptos will only be secure in your wallet, but these cryptocurrency wallets are usually vulnerable to hacking.
In this article, we will discuss the types of crypto wallets and share some helpful tips for picking a secure one. Treating your crypto wallets with extreme care is essential since their security measures directly affect the protection of your digital assets.
What is a Crypto Wallet?
Any digital asset, such as a cryptocurrency, can be safely stored, managed, and interacted with the help of a cryptocurrency wallet. In lay terms, it allows you to retrieve cryptocurrencies you possess on a blockchain.
In addition, they facilitate blockchain-based cryptocurrency transactions. Some wallets even enable users to transact in a limited fashion with their crypto assets, such as making purchases or interacting with decentralized applications (dapps).
Crypto wallets, in contrast to wallets used for fiat currency, do not hold the coins themselves. Instead, they only contain the private keys required to access and move the amounts recorded on the blockchain.
There are two primary parts to any crypto wallet:
- The Public Keys.
- The Private Keys.
The Public Key
This key sometimes called a wallet address, is an individually generated string of alphanumeric characters that specifies where a person should send the digital currency.
You can compare a public key to a bank account number, as you can freely share it with anybody who wishes to give you cryptocurrency. On the other hand, the private key is a cryptographic secret code that grants access to and ownership of blockchain-stored money.
The Private Key
This key can be likened to your ATM or bank transaction pin, meaning you can’t give anyone access. To validate and authenticate cryptocurrency transactions, users must broadcast them to the blockchain network after digitally signing them with their private keys.
Since the private key allows access to the linked money, you should always safeguard it and keep it a secret. The security of a user’s cryptocurrency depends on the security measures taken to keep it.
While it is possible to keep crypto on an exchange, it is only advisable if you are dealing in small quantities or trading often. When dealing with higher sums, users should remove most of their funds from a crypto wallet (either a hot or cold wallet).
This way, you can control your money and data since you hold the private keys.
Types of Crypto Wallets
It’s essential to remember that you’re not stuck with just one option when it comes to the crypto wallets out there. You can categorize your wallets into the following categories, depending on their storage medium and method:
- Hot Crypto Wallets
- Mobile Wallets
- Web Wallets
- Desktop Wallets
- Cold Crypto Wallets
- Paper Wallets
- Hardware Wallets
- Custodial Wallets
- Non-custodial Wallets
Hot Crypto Wallets
Hot wallets are the most popular option for consumers who like to have instant access to their cryptocurrency. The term “hot wallet” refers to digital currency storage solutions that may be accessed from any internet-connected device.
Since they provide immediate access to your cryptocurrency, they are ideal for routine transactions. However, their online connectivity makes them more susceptible to malicious activities like hacking, virus distribution, and phishing.
To put it another way, hackers have an easier time gaining access to cash kept in hot wallets because of this. Better options exist than a hot wallet for storing significant sums of Bitcoin.
Hot wallets come in various forms, each with its own set of advantages and disadvantages, and they include:
Mobile Crypto Wallets
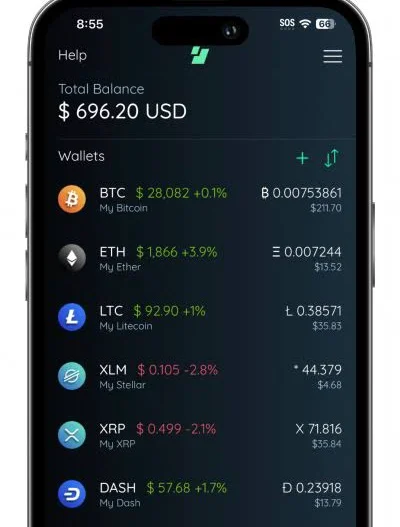
A mobile wallet is a digital currency wallet that can be accessed from a mobile device like a smartphone or tablet. A “hot wallet” program must be downloaded and run on the mobile device for this to work.
Mobile wallets provide users with more versatility when trading cash but pose significant security dangers. The most obvious perk of a mobile wallet is the ability to take your cryptocurrency purchasing power with you wherever you go.
The straightforward applications simplify acquiring, storing, trading, spending, and managing your cryptocurrency from your mobile device. Some examples of mobile wallets are Coinomi, Mycelium, Edge, Trust, and Electrum.
Web-based wallets
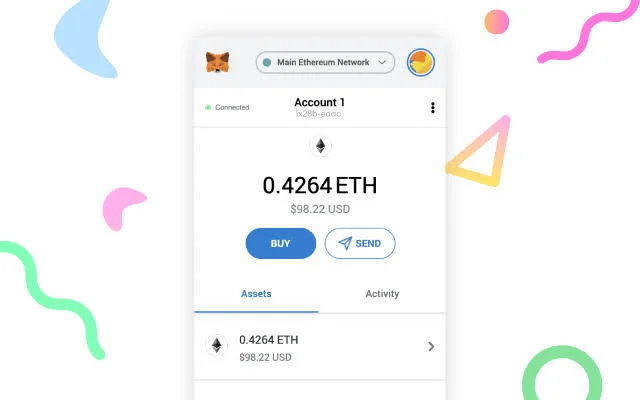
Another type of wallet you can find today are web wallets. Web wallets give users easy access to their assets using a web browser and are often offered through a cryptocurrency exchange.
Web wallets enable access to your cryptocurrency from any device with an internet connection and a password. When using an online wallet, the hosting service is the one that has the private keys to your digital currency.
They may include a transaction log, an address book, and the ability to connect to third-party services and decentralized apps (DApps). They’re convenient for making speedy transactions and small investments. Examples include MetaMask and Coinbase.
Desktop wallets
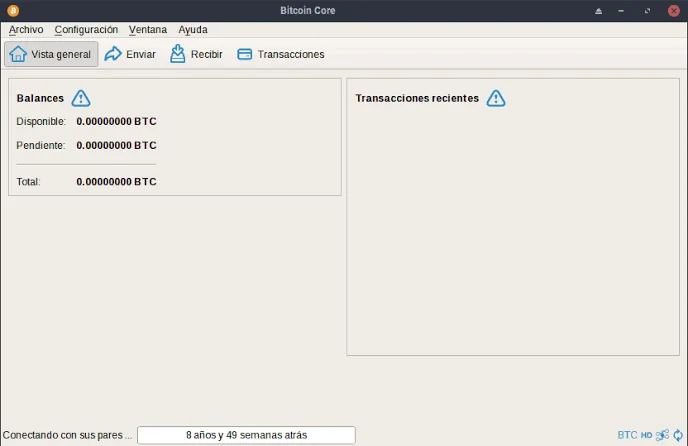
A desktop wallet is a crypto wallet installed on a desktop or laptop computer. They offer better protection than online or mobile wallets and give users direct access to their private keys.
People that value security and prefer to keep their cryptocurrency locally on their computers tend to favour desktop wallets. They provide privacy and anonymity, are simple to use, and don’t involve any other parties.
However, the computer has to be regularly backed up. Examples of desktop wallets include Exodus, Bitcoin Core, and Electrum.
Cold Crypto Wallets
Another type of crypto wallets are cold wallets. The term “cold wallets” refers to cryptocurrency wallets that are not online, commonly referred to as “cold storage” or “offline wallets.” As a result, they act as vaults that you may utilize for regular transactions.
Specific cold wallets may connect to the internet while maintaining their essential functions. They offer more protection by storing the private keys offline and away from internet dangers.
Therefore, it is evident that those with more crypto assets will gain more from cold wallets. The main types of cold wallets are:
Paper Wallets
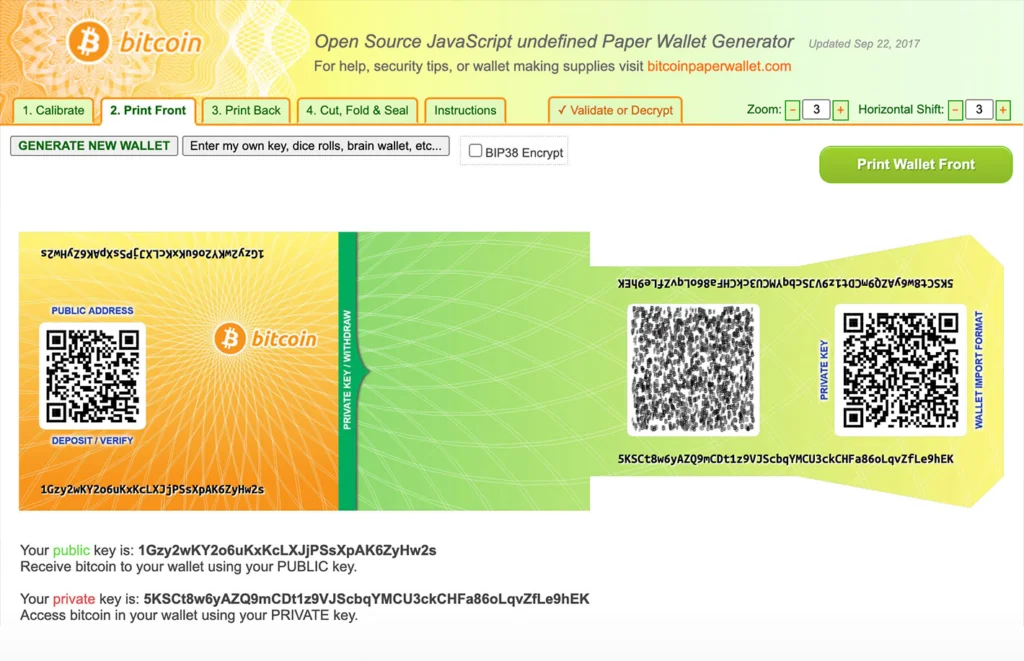
A paper wallet is a type of crypto wallet that is a physical storage medium containing private and public keys. Since these keys are protected against phishing attempts, they are safer than a traditional “hot wallet” for storing cryptocurrency in many respects. However, doing so exposes the money to the risk of losing forever if the paper is lost or damaged.
If you misplace the paper, you might lose access to your cryptocurrency. Another disadvantage of paper wallets is that transferring only a portion of a payment is difficult. In addition, the slow speed of paper wallet transactions is a significant drawback.
It’s easy to make your own safe, printable paper wallet, yet some people still prefer the tried-and-true method of using paper and pen. Some examples of sites you can make your printable wallets include BitcoinPaperWallet.com and WalletGenerator.Net.
Hardware Wallet

In contrast to software-based wallets, hardware wallets store and manage private keys and public addresses offline. A hardware wallet is a portable attachment (often a USB or Bluetooth device) that contains a user’s keys.
Additionally, it requires the user to physically sign transactions by pressing a button on the device, making them immune to hacking attempts. They offer more protection than hot wallets and greater convenience than paper wallets.
However, they can’t be used online and must be physically interacted with to process payments. Due to their secure physical construction, hardware wallets resist theft via unauthorized access.
Some of the most widely used hardware wallets include Ledger Nano S and Trezor.
Custodial Wallet

Another important type of crypto wallet to take note of are custodial wallets. Online cryptocurrency wallets often take the form of custodial wallets. These wallets are widely available on cryptocurrency exchanges, and many people like them because of their simplicity and convenience.
Custodial wallets require that users give up custody of their tokens and rely on the exchange to store their private transaction signing keys. The security of the private keys and the money held in a custodial wallet is the responsibility of the wallet provider.
They often employ encryption and two-factor authentication (2FA) to safeguard user accounts. An example of a custodial wallet is Binance.
Non-custodial Wallet

When users control their private keys, the wallet is considered non-custodial or self-custody. This type of crypto wallet provider has no access to or holds over the user’s private keys; the user is responsible for keeping them safe.
Users must often have more technical expertise and initiative to manage their private keys in a non-custodial wallet effectively.
They, however, provide a higher level of protection, anonymity, and freedom from outside interference. Hardware wallets, software wallets in which the user retains essential private control, and paper wallets are all examples of non-custodial wallets. Some non-custodial wallets include Zengo, Exodus, Wasabi, etc.
Tips to Identify a Secure Crypto Wallet
- Open Source
- Security Features
- Private Key Control
- Reputation and Reviews
- Backup and Recovery
Open Source
Another tip for identifying a secure crypto wallet is checking if it is an open-source wallet. The source code for open-source wallets is easily accessible, allowing developers and security professionals to check it for flaws. This openness improves the wallet’s safety and credibility.
Security Features
It is essential to check the crypto wallet’s encryption and other safety measures. Try to find wallets with features like two-factor authentication (2FA), biometric authentication, private key encryption, and hierarchical deterministic (HD).
These features enhance safeguards against intrusion and other vulnerabilities.
Private Key Control
Make sure you have complete access to your private keys with the wallet. Holding private keys alone grants you complete control and ownership of your cryptocurrency holdings.
If a wallet requires you to share your private keys or store them on their servers, you should avoid it.
Reputation and Reviews
Learn as much as you can about the wallet by reading reviews and getting comments from current users. Examine the wallet’s security record and user reviews on credible cryptocurrency forums, social media platforms, and review websites.
Backup and Recovery
Make sure the wallet offers a safe and secure method of backup and recovery. Backup features like recovery phrases should be available in every good wallet. You can use this backup to reaccess your funds if your device is lost, stolen, or damaged.
Conclusion
It is crucial for you to carefully select a trustworthy crypto wallet to keep your digital assets safe. There are important considerations to make while choosing a secure wallet, regardless of whether it is a hot wallet, cold wallet, custodial wallet, or non-custodial wallet.
Before settling on a crypto wallet, you should evaluate how vital factors like usability and safety are to you. Additionally, consider how readily available you need your crypto to be and how much you are ready to sacrifice in terms of security. To help you choose the best and most secure wallet, we have compiled the types of crypto wallets to make it easier.
Since keeping a lot of money in a single crypto wallet is unsafe, many people find that using a mix of cold and hot wallets is the best way to achieve a happy medium between the two, convenience and security.
