Hayden Adams, the founder of decentralized exchange (DEX) Uniswap, has warned the cryptocurrency community concerning a fraudulent scheme that uses wallet addresses disguised as Ethereum Name Service (ENS) domains.

Adams issued a warning on X on February 14 regarding fraudsters posing as his Ethereum wallet. The executive explained that the fraudsters registered an address for his wallet with the extension.eth under the guise of an ENS wallet.
In addition, the proprietor of Uniswap stated that pasting his wallet address into certain user interfaces would return as the top search result in an ENS match unrelated to his actual address.
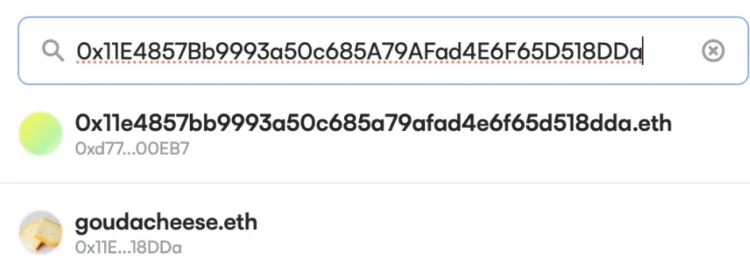
The apparent objective of the scheme is to deceive senders of digital assets, who may inadvertently deliver their cryptocurrency to the incorrect recipient’s address rather than the intended one.
Adams strongly recommended that user interfaces implement filtering mechanisms to eliminate these addresses to prevent potential losses from the attack vector.
Taylor Monahan, the founder of Ethereum wallet manager MyCrypto, stated in a post that the early days of the wallet service MyEtherWallet also utilized the same fraud vector, even though it appears to be an extremely recent development. Additionally, according to Monahan, they “broke” registrations and resolutions for names commencing with “0x” at the time.
Nick Johnson, the founder and main developer of ENS, also commented on the scam vector, stating that name autocomplete should not occur in interfaces. The developer noted that this was “far too dangerous” and that their user experience guidelines discourage such conduct.
A month ago, cryptocurrency investors began receiving emails purporting to be from fraudsters posing as prominent Web3 companies. Scammers orchestrated an extensive email campaign on January 23 that promoted illegitimate airdrops under the guise of Cointelegraph, WalletConnect, Token Terminal, and other cryptocurrency companies.
Subsequent investigation revealed that a security vulnerability at the email marketing company MailerLite was the root cause of the phishing attack. The company verified on January 24 that social engineering assisted hackers in gaining access to Web3 accounts.
The research team of the analytics platform Nansen estimated that since the campaign began, the fraudster’s phishing wallet has received approximately $3.3 million in inflows.
