Protocol for Humanity’s Proof, Worldcoin On July 28 issued its audit results amid growing criticism of its data acquisition procedures.

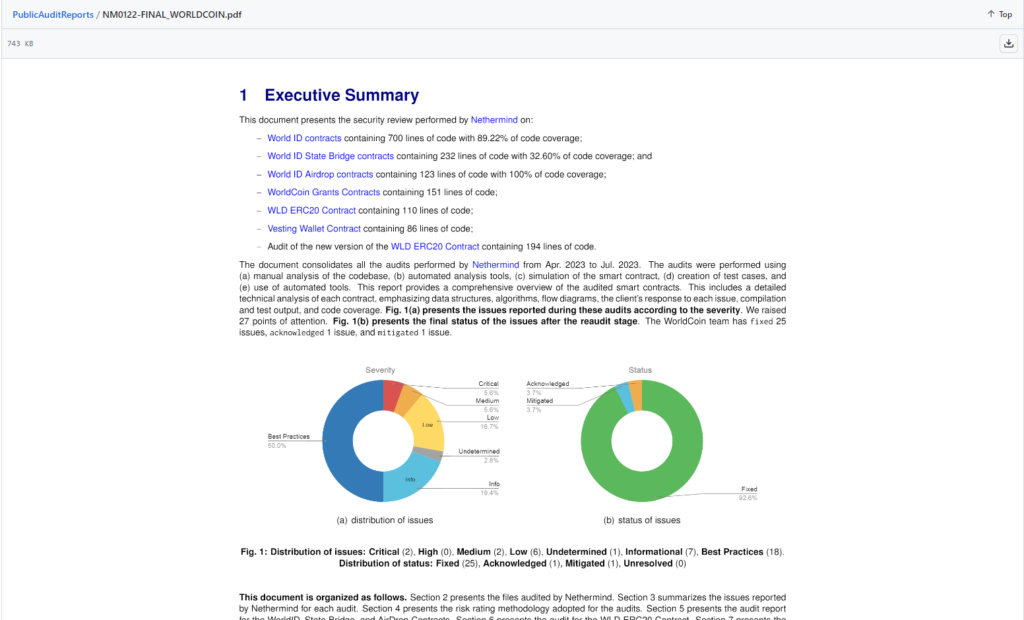
Security consultancy firms Nethermind and Least Authority produced the new studies. Nethermind discovered 26 security flaws in the protocol, of which 24 were “identified as fixed” during the verification phase, one was mitigated, and two others were acknowledged, according to a Worldcoin release that was published alongside the findings.
Least Authority identified three problems, and six recommendations were made; all of these problems “have been resolved or have planned resolutions,” according to the release.
Worldcoin originally gained notoriety in 2021 when it declared that it would offer free tokens to any users who could prove they were human by having their irises scanned by a technology dubbed “Orb.”
Sam Altman, a co-founder of the AI software company OpenAI, contributed to the project’s founding. At the time, Altman and other team members contended that if users didn’t discover a means to confirm that AI bots are human without compromising their privacy, they would become an expanding nuisance on the internet.
The protocol specifies that The Orb creates a hash rather than a copy of the user’s iris scan.
After nearly two years of development and beta testing, Worldcoin had its public launch on July 25. But soon after, criticism of it started to spread. According to reports, the UK’s Information Commissioner’s Office (ICO) was debating whether to launch an investigation against the initiative for allegedly breaking the nation’s data protection regulations.
The legitimacy of Worldcoin was also questioned by the French data protection regulator CNIL. Some crypto community members believed that the project’s introduction signaled the beginning of a dismal future in which privacy would be completely eliminated.
Others believed it to be a crucial step in defending people against bad AIs. The new audit reports address a broad range of security issues, such as DDoS attack resistance, case-specific implementation mistakes, key storage and correct management of encryption and signing of keys, data leakage and information integrity, among others.
Some problems were discovered due to dependence on Semaphore and Ethereum, such as “elliptic curve precompile support or Poseidon hash function configuration,” the announcement said.
With the exception of one, all problems have been resolved, have been mitigated, or are scheduled for resolution. One security flaw that had not been resolved at the time of verification had a severity of “undetermined” and is marked as “acknowledged.”
