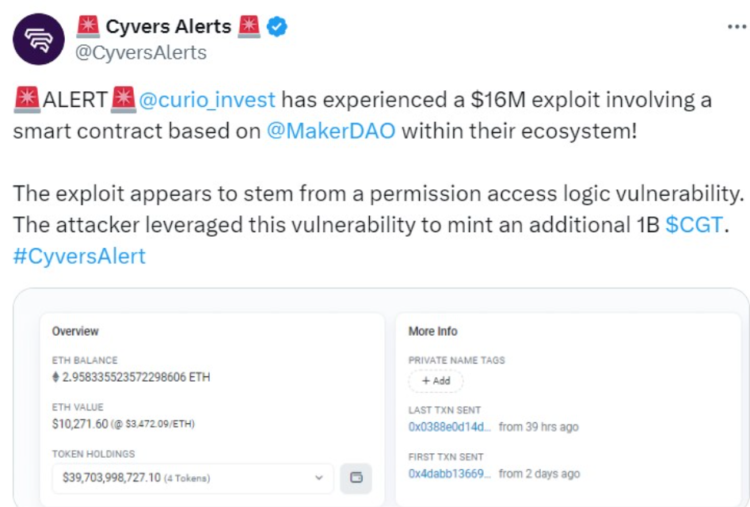
A hacker was able to steal $16 million worth of digital assets from real-world asset (RWA) liquidity firm Curio due to a smart contract exploit involving a critical vulnerability associated with voting power privileges.

Curio notified its community regarding the vulnerability and emphasized its efforts to rectify the situation. An organization stated that a smart contract built on MakerDAO and utilized by Curio had been compromised.
Nevertheless, the organization guaranteed its clientele that the vulnerability solely impacted the Ethereum component and that every Polkadot and Curio Chain transaction remained secure.
The Web3 security firm Cyvers has estimated that the exploit has caused approximately $16 million in damages. According to the security firm, the exploit exploited a “permission access logic vulnerability.”
A compensation plan for afflicted users and a post-mortem of the exploit were both published by Curio on March 25. Curio emphasized in the report that the issue was attributable to a deficiency in the privilege access control for voting power.
By doing so, the assailant obtained a limited quantity of Curio Governance (CGT) tokens, which granted them entry and enhanced their ability to vote on the smart contract for the project.
The adversary executed a sequence of operations made possible by the elevated voting authority, which ultimately enabled the implementation of arbitrary actions within the Curio DAO contract. The consequence was the illicit production of one billion CGT.
Curio stated in the report that every penny lost due to the exploit will be refunded. CGT 2.0 is the name of the new token that the group announced it would issue. The group pledged to fully return all CGT holders’ funds using the new token.
Curio has declared that it will implement a fund compensation program for liquidity providers. According to the team, the payment schedule consists of four 90-day stages. This may imply that completing the payment process could take up to a year. They penned:
“The compensation program will consist of 4 consecutive stages, each lasting for 90 days. During each stage: compensation will be paid in USDC/USDT, amounting to 25% of the losses incurred by the second token in the liquidity pools.”
Additionally, the organization declared that it would compensate white hat hackers who assist in the recovery of the lost funds. According to the team, in the initial phase of fund recovery, hackers may be eligible to receive a reward equal to 10% of the funds recovered.
