Prisma finance reports $540K still at risk from accounts yet to revoke the smart contract responsible for last week’s $11.6 million exploit.

Prisma Finance, a decentralized finance (DeFi) firm, reports that $540,000 remains in accounts from which the smart contract liable for the $11.6 million breach last week has yet to be revoked.
In the interim, the purported “white hat” hacker responsible for the breach asserts that the reimbursement process will be postponed until the company issues an apology and publicly discloses the identity of their team.
On April 1, core contributor “Frank” stated in a “path forward” post that while the return of funds will remain a priority, un pausing the protocol is. However, he added that all users must first ensure the security of their wallets and positions.
Two MigrateTroveZap contracts, which were intended to migrate user positions from one trove manager to another, were implicated in the multimillion-dollar exploit that compromised the protocol last week, according to a post-mortem post from Prisma that was last updated on March 31.
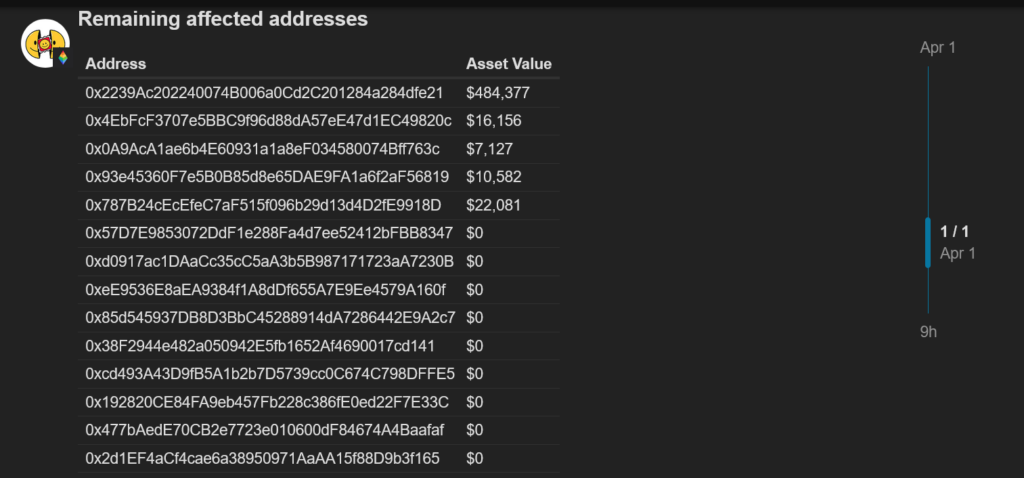
Frank noted, however, that five of the fourteen accounts that had not yet revoked the compromised smart contract remained “at risk” with open trove positions exceeding $500,000.
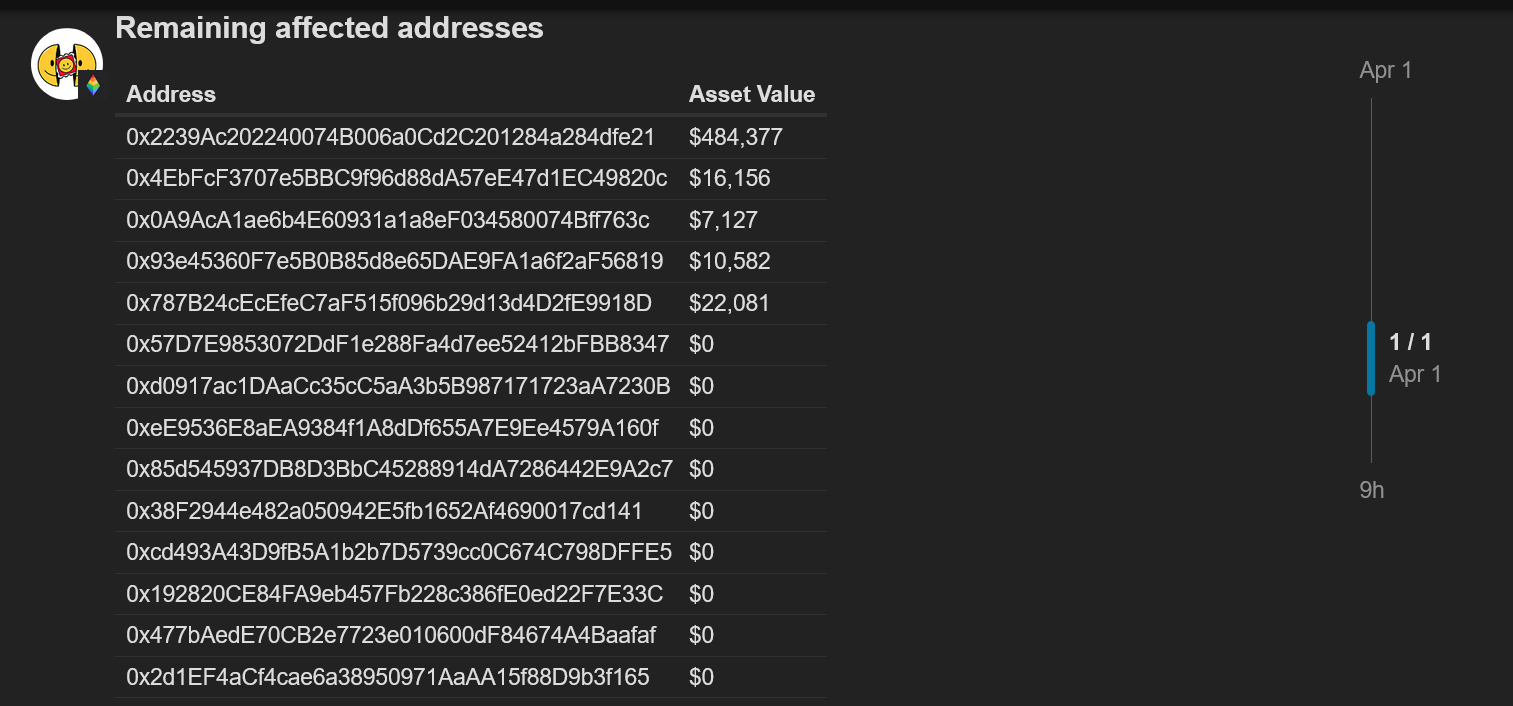
“Of the affected Troves several have revoked the contract containing the vulnerability with ~$540k of collateral still at risk at the time of writing.”
Prisma is a decentralized borrowing protocol where users can obtain and maintain loans using “troves” (Ethereum addresses).
The largest address marked “at risk” contains $484,380, whereas the remaining four contain funds ranging from $7,120 to $22,080.
Frank elaborated that continuing to “conserve additional reserves” was a component of its “path forward” while Prisma endeavored to recover the stolen funds. A revised proposition to decrease staked revenue from vPRISMA and liquidity from POL was introduced on April 1.
Additionally, Prisma emphasized that the compromised contract was isolated from the core protocol and had no intention of resuming it until all user funds had been restored.
Identify Yourselves And Confess Publicly, Hacker Demands
In the interim, the purported “white hat” has levied allegations against the DeFi firm, asserting that it acted dishonestly and threatening to withhold the funds unless the company issues a public apology.
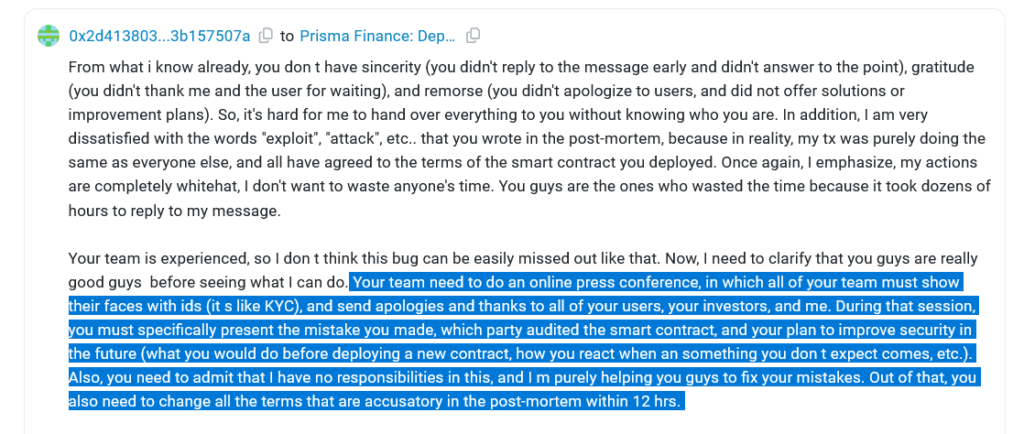
An element of this apology consists of Prisma hosting an online conference wherein the entire team must present identification and face-to-face statements apologizing to all users and investors for the inadequate auditing of its smart contract.
In an on-chain message dated March 30, the exploiter stated the following:
“During that session, you must specifically present the mistake you made, which party audited the smart contract, and your plan to improve security in the future.”
The exploiter further requests that Prisma acknowledge that they bear “no responsibilities” in the ordeal and are merely assisting Prisma in correcting its error.
In response, Prisma emphasized that the exploiter has not yet reimbursed any funds as an act of good faith. The two parties then engaged in further discussion via on-chain messaging.
“There is little evidence that we can judge you on that you are sincere in your intention to return the assets. Most genuine white hats would have returned at least some of the funds by now.”
Since the attack, blockchain security firms Cyvers and Peckshield have observed that the hacker has begun exchanging the stolen funds for Ether (ETH). Approximately 200 Ether were transmitted to Tornado Cash, an OFAC-approved cryptocurrency mixer.
DefiLlama reports that Prisma Finance had approximately $220 million in total value secured on its protocol before the exploit; that amount has since dropped to $87 million.
