Following a $6.4 million digital assets exploit from the Seneca stablecoin platform, the hacker has returned over $5 million after the project pledged a 20% bounty to the hacker.

Multiple blockchain security firms identified the vulnerability in the stablecoin protocol on February 28. Enterprises such as CertiK issued advisories to users regarding the vulnerability, imploring them to revoke authorizations from a specific address on the Ethereum and Arbitrum networks.
Initial losses were estimated at $3 million; however, it was discovered that more than 1,900 Ether, valued at approximately $6.4 million, had been stolen from the exploit.
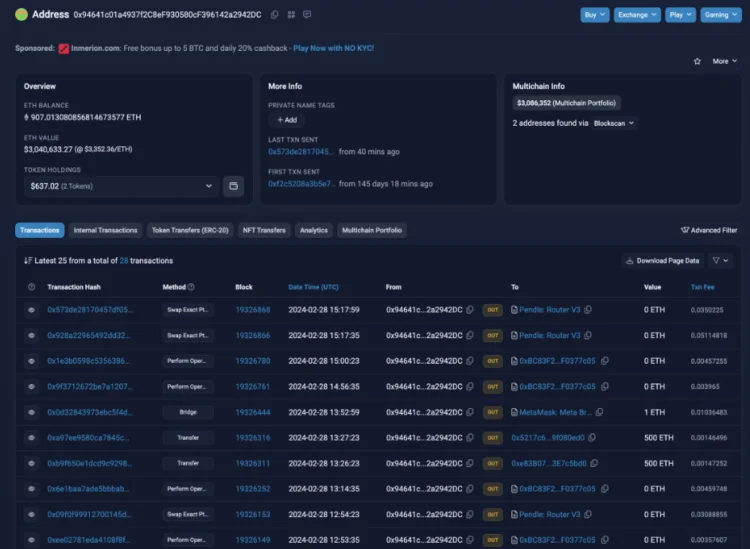
According to security analysts at CertiK, the exploit occurred because of a critical “call” vulnerability in the smart contract of the protocol. The attacker could have exploited this vulnerability to initiate external communications to any given address.
Furthermore, the contracts for the project lacked a procedure that would have permitted the team to “pause” it. As a consequence, users are required to revoke permissions.
Seneca stated that it is investigating with the assistance of specialists. A bounty of $1.2 million was also offered in exchange for recovering the misappropriated funds.
On February 29, Seneca requested in an on-chain message that the intruder transfer 80% of the stolen funds to an Ethereum address while permissibly retaining 20%.
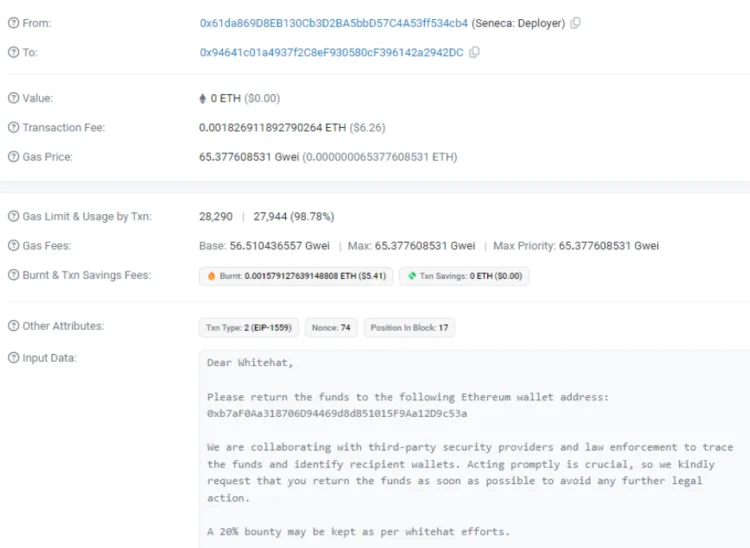
Seneca stated in the message that it is conducting joint efforts with law enforcement and security providers to trace the funds. It advised the infiltrator to reimburse the funds to evade potential legal ramifications. It stated, “Timely action is critical; therefore, we respectfully request that you return the funds without delay to prevent any additional legal proceedings.”
Hours after Seneca sent the message, the intruder returned to the wallet address Seneca specified approximately 1,537 ETH, worth roughly $5.3 million.
The hacker retained 300 ETH, valued at about $1 million, and agreed to the 20% bounty that Seneca protocol offered. Subsequently, the exploiter split the ETH between two distinct addresses.
